Data Protection Goals
The Pros and Cons of Formalising Privacy Requirements for technical Systems
martin.degeling@ruhr-uni-bochum.de
München/Munich, 1.11.2013
München/Munich, 1.11.2013
Information and Technology Tanagement
Institute for Work Science
Ruhr-University Bochum
Institute for Work Science
Ruhr-University Bochum

Data Protection deals with informational Privacy
Privacy and Data Protection
Coined by lawyers to regulate IT systems
in contrast to e.g. Rössler, B. (2005). The value of privacy. (R. D. V. Glasgow, Trans.)
(English ed.). Cambridge, UK ; Malden, MA: Polity.
(English ed.). Cambridge, UK ; Malden, MA: Polity.
the individual (fundamental but negotiable) right for
informational self-determination
BverfG. (1983). Urteil vom 15. Dezember 1983.
Referes to
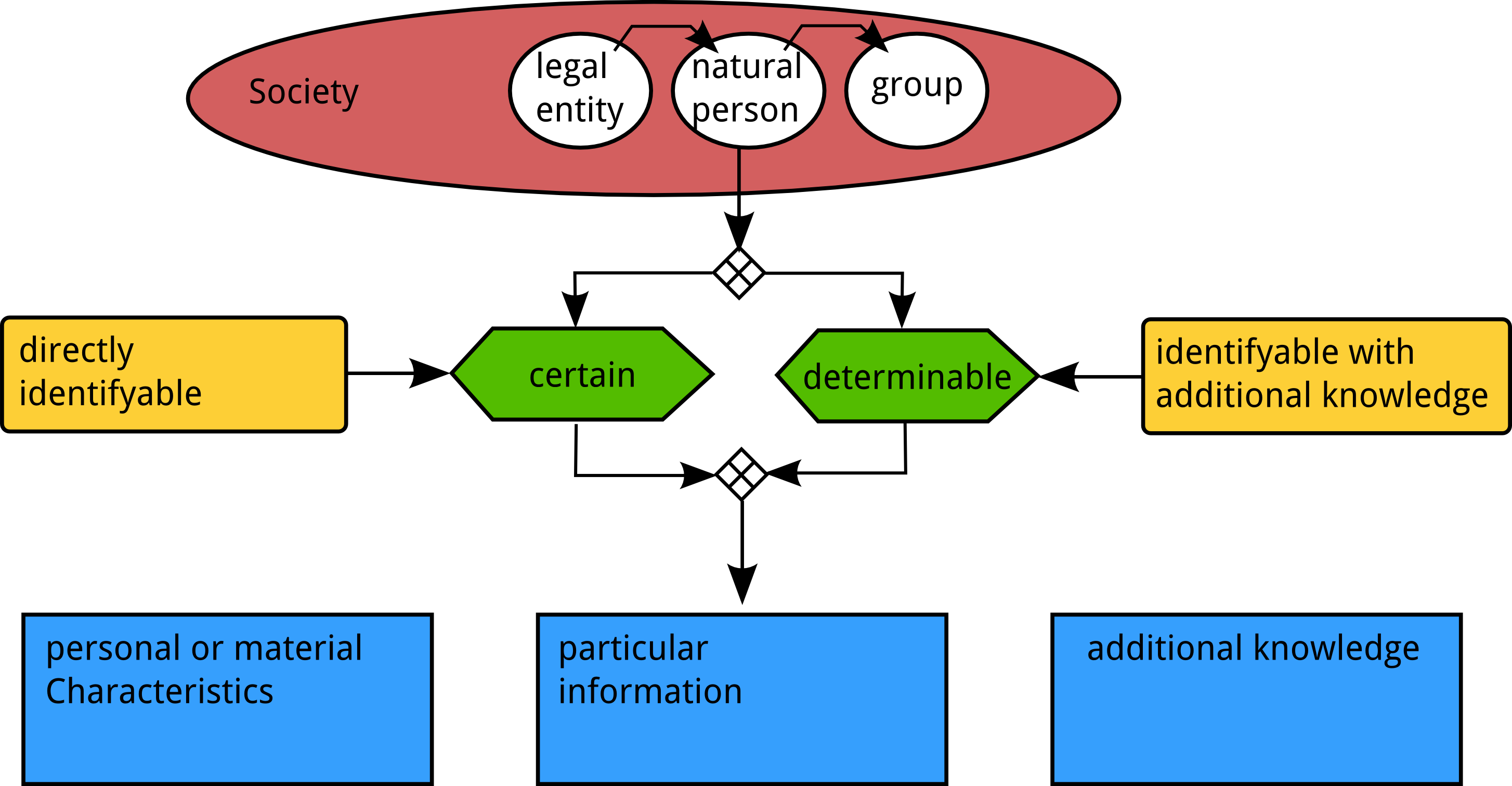
A Model of §3 Abs. 1 BDSG (Federal Data Protection Law in Germany)
--
From a lecture on "Data Protection" for students of computer science
From a lecture on "Data Protection" for students of computer science
Quest: Translating Laws to Models for IT
Privacy Breach: Improper Access
My university could use the data
to verify my traveling an call Andreas
to verify my traveling an call Andreas
Privacy Breach: Use for secondary purpose
A commercial mail provider could
send Andreas product information about
alternative mail clients.
send Andreas product information about
alternative mail clients.
Privacy Breach: Use group information for
secondary purpose
secondary purpose
Google could invite all recipients to connect to
each other in their new google+scholar
each other in their new google+scholar
The General Privacy Problem in there
I have no control about how information about me is processed by the
service providers of my recipients. Technically they could do anything described.
service providers of my recipients. Technically they could do anything described.
1. Rost, M. (2013). Zur Soziologie des Datenschutzes.
Datenschutz und Datensicherheit, 37(2), 85–91.
Datenschutz und Datensicherheit, 37(2), 85–91.
Data Protection should reduce power asymmetries
between individuals and organisations¹
The Requirement to IT from Data Protection
How can misuse of personal
information be prevented?
- How much information flow should still be possible?
- How can misuse be detected?
- What defines un-authorised access?
- Who should have control about each part of the system?
- What data is necessary for operation?
- ...
Guidlines for informational privacy problems were first developed from a
juristic perspective
juristic perspective
Bizer, J. (2007). Sieben Goldene Regeln des Datenschutzes.
Datenschutz und Datensicherheit - DuD, 31(5), 350–356.
doi:10.1007/s11623-007-0133-x
Datenschutz und Datensicherheit - DuD, 31(5), 350–356.
doi:10.1007/s11623-007-0133-x
Definig Data Protection Guidelines
Reidenberg, J. R. (1994). Setting Standards for Fair Information
Practice in the US Private Sector. Iowa L. Rev., 80, 497
Practice in the US Private Sector. Iowa L. Rev., 80, 497
- Notice/Awareness
- Choice/Consent
- Access/Participation
- Integrity/Security
- Enforcement/Redress
Fair Information Practices
Golden Rules Of Data Protection
- Lawfulness
- Consent
- Purpose
- Minimization/Deletion
- Transparency
- Security
- Control
The Problem with the guidelines
following Rost this is a problem of different
spheres in a functional differentiated society
spheres in a functional differentiated society
translation from guidelines to principles
lead to ambiguities
How to ensure that the legal requirements are technically implemented?
following: Rost, M., & Storf, K. (2013). Zur Konditionierung von Technik und Recht
mittels Schutzzielen. In M. Horbach (Ed.), Proceedings (Vol. 220, pp. 2149–2166). Koblenz: Springer.
mittels Schutzzielen. In M. Horbach (Ed.), Proceedings (Vol. 220, pp. 2149–2166). Koblenz: Springer.
It is only allowed to store data as long
as it is needed for the purpose it is
collected for
as it is needed for the purpose it is
collected for
Deletion = removing access (moving to
trash folder) THEN wiping it from a hard disk
THEN proceed with deletion in
all backups and copies on redundant devices
trash folder) THEN wiping it from a hard disk
THEN proceed with deletion in
all backups and copies on redundant devices
Legal Perspective on Purpose
Translation in to technical Context
Operationalize Data Protection Guidelines
Data Protection Goals
.png)
Rost, M., & Pfitzmann, A. (2009). Datenschutz-Schutzziele — revisited.
Datenschutz und Datensicherheit - DuD, 33(6), 353–358.
doi:10.1007/s11623-009-0072-9
Datenschutz und Datensicherheit - DuD, 33(6), 353–358.
doi:10.1007/s11623-009-0072-9
Datenschutz-Schutzziele
focus on keeping an organisational
infrastructure in tact
.png)
the CIA triade
New Data Protection Goals
- Transparency
- Unlinkability
- Ability to intervene
focus on the data and the processing workflows.
.png)
Integrity
Ability to Intervene
make sure everything
works correct
works correct
allow data subjects to
intervene in the data processing
of their data
intervene in the data processing
of their data
design workflows that are capable
of changing data sets e.g. delete
data on all clients; or offer choice for
ad programms
of changing data sets e.g. delete
data on all clients; or offer choice for
ad programms
- protect against cyber attacks
(or spam)
- log access
(or spam)
- log access
.png)
Unlinkability
Transparency
prevent secondary use
allow data subjects
to know which data is processed
for which purpose
to know which data is processed
for which purpose
- physcially separated data storages e.g.
mail-serverdata and other data
- usage of different accounts for different
services
mail-serverdata and other data
- usage of different accounts for different
services
- privacy dashboards e.g. showing
how much you mailed to whom
how much you mailed to whom
Availability
.png)
Confidentiality
- use redundant systems to prevent
data loss
- allow access from mulitple interfaces
(web, mail-client)
data loss
- allow access from mulitple interfaces
(web, mail-client)
data should be (easily) accessible
- implement access control
to limit access (e.g. do not allow
admins to read mails)
- use encryption (on all levels)
to limit access (e.g. do not allow
admins to read mails)
- use encryption (on all levels)
reduce access rigts
as much as possible
as much as possible
Conclusions
The Pros and Cons of DPGs
The Goal of Data Protection Goals
- support communication between legal and technical experts
by building a common language - can be used to normalize an understanding of privacy
in technical processes and make measures comparable - supporting a proactive, privacy-aware technology
development
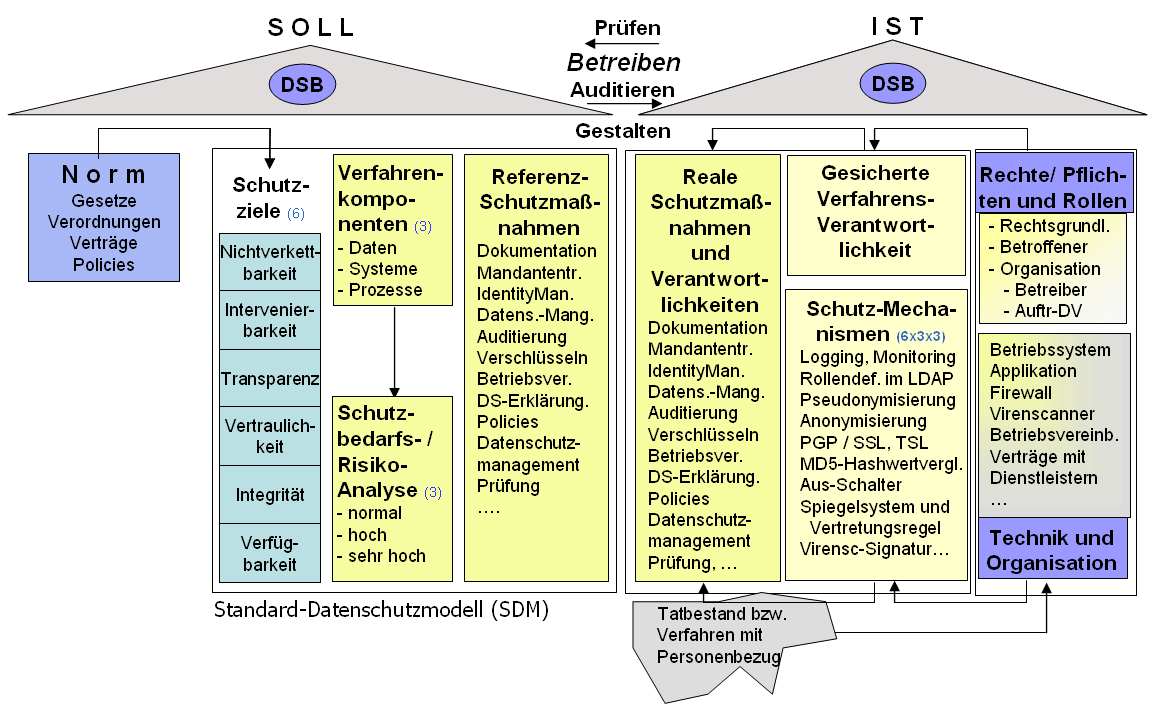
The Standard Data Protection Model
Image Source: http://www.datenschutzziele.de/sdm/work.html
Activities developed from Data Protection Goals
For : Data, Systems and Processes
Probst, T. (2012). Generische Schutzmaßnahmen für Datenschutz-Schutzziele.
Datenschutz und Datensicherheit - DuD, 36(6), 439–444.
Datenschutz und Datensicherheit - DuD, 36(6), 439–444.
Changing the game
DPGs are more proactive (like PrivacyByDesign and PETs)
It is no longer necessary to evaluate what is technically
possible and remove features,
but to include data protective features from the beginnen
It is no longer necessary to evaluate what is technically
possible and remove features,
but to include data protective features from the beginnen
Rost, M., & Bock, K. (2011). Privacy By Design und die Neuen Schutzziele.
Datenschutz und Datensicherheit, 35(1), 30–35.
Datenschutz und Datensicherheit, 35(1), 30–35.
- .. only indirectly help reducing power asymmetries
- .. do not support a broader undestanding of privacy
besides the known invidual and information focussed
DPGs
Although conceptualized with a broader focus
DPGs are more a meachnism of regulating
information flows to achieve
the optimized balance between
privacy and interestes of data processors
Privacy is not just an information
flow that has to be regulated
checklists offer backdoors for service providers
to be able to avoid discussions about
the influence of their practices on privacy
DPGs make it easy to avoid discussions
although the data protection discussions and its
normative definition of privacy are not purely focus
on the individual (data-subject) DPGs do not
allow broader notions of privacy
The Assumption of the
Autonomous Data Subjects
That's it
thanks
although there are detailed measurements those
do not support individual autonomy but a design
for a 'one size fits all' understanding of privacy
DPGs can be 'one size fits all'